Support 0800 368 1831
Sales 01225 300 330
-
How we help
Technical consultancy
-
Certified Guidance
Tap into tailored expertise, certified by Microsoft
-
Migration Planning and Support
Become a better business by migrating to Microsoft Azure
-
Growth and Scalability
Make Azure your foundation for innovation, security and scalability
Assurance and Security
-
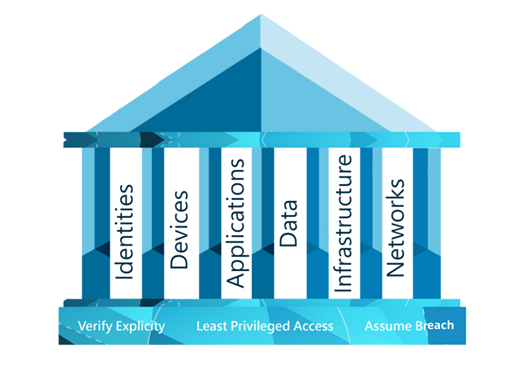
Security and Risk Management
Protect your business and its assets against evolving threats
-
Regulatory Assurance
Have confidence innovating under the spotlight of industry regulation
Innovation
-
Build for Tomorrow
Futureproof your business with AI technology
-
Data Modernisation
Transform your business with data-driven insights, automation and AI
Getting AI Ready
Adopting AI can seem complex, but it doesn’t have to be. The secret to successfully implementing AI is putting the right foundations in place.
Find out how -
Certified Guidance
-
What we do
Microsoft Azure
Data & AI
Microsoft Modern Work
Getting AI Ready
Adopting AI can seem complex, but it doesn’t have to be. The secret to successfully implementing AI is putting the right foundations in place.
Find out how -
Explore
Company
- Talk to our experts