We’re excited to announce that Cloud Direct secured the Threat Protection, Identity and Access Management, and Information Protection and Governance Advanced Specialisations.
We’ve managed to secure not one, but three more Microsoft Advanced Specialisations! Achieving these Advanced Specialisations highlights our Microsoft Security knowledge, experience, and expertise.
The Advanced Specialisations are awarded following a review by Microsoft of our technical expertise and project experience with various Microsoft Security Technologies:
- Threat Protection Advanced Specialisation: Microsoft Threat Protection, Microsoft Cloud App Security and Sentinel Workloads
- Information Protection and Governance Advanced Specialisation: Microsoft Information Protection workloads
- Identity and Access Management Advanced Specialisation: Microsoft Identity workloads with Azure Active Directory (Azure AD)
“Delighted to have achieved three new ‘Advanced Security Specialisations’ from Microsoft. It’s a great validation of the investment Cloud Direct continues to make in security – and adds nicely to our existing Sentinel SIEM/SOAR capability. There’s no doubt that security is increasingly at the forefront of customers minds – especially as they centre on digital and cloud. Well done team Cloud Direct for this relentless and focused learning.” – Brett Raynes, CEO
Achieving an advanced specialisation is a rigorous process. There are a stringent set of requirements that must be assessed and verified by Microsoft and a third-party vendor. Only partners that meet the criteria below can earn various advanced specialisations:
- Be a Microsoft Gold Partner
- Have skilled staff with the appropriate qualifications
- Have proven experience in Security delivery
- Achieve required performance thresholds
Theses advanced specialisations are in addition to the existing advanced specialisations we have been awarded by Microsoft – Teams Calling, Azure Virtual Desktop and Azure Specialist for ISV.
Ready to transform your security with one of Microsoft’s leading partners?
With security being a huge priority for many businesses, ensuring that you have the right partner is crucial to protecting your business. Having achieved these three Advanced Specialisations, you’ll be able to reap the benefits of our knowledge and expertise in these specific solution areas. But that’s not all. We’ve also achieved other security accreditations which you can view here.
Security is at the heart of our solutions, and we’ve completed numerous successful security projects for our customers. These range from helping businesses adopt Azure Sentinel to improving their Secure Score.
Ready to assess your security? Get in touch to talk to one of our Microsoft Security Experts.
We all know a castle and moat security approach just doesn’t cut it anymore. That’s why you’re here, right? You’re ready to have a security strategy in place that’s aligned with the modern, hybrid work environment.
Zero Trust is an end-to-end security strategy that’s based on ‘never trust, always verify’, and has been adopted by millions of organisations across the world to protect their technology ecosystem. If you’d like to find out more about what Zero Trust is and why you should look at adopting it within your organisation then check out our Beginner’s Guide to Zero Trust.
In this blog, we’ll be running through the Microsoft technologies available to help you implement a Zero Trust security strategy. We’ll dive into the specific technologies you can use to start defending the six elements of Zero Trust; identities, devices, applications, data, infrastructure, and networks.
Identities
Identities representing people, services or IoT devices, are the common dominator across network, endpoint and applications. In a Zero Trust strategy, identities function as a powerful and flexible way to control access to data. Microsoft suggests that before an identity attempts to access a resource, you should:
- Verify the identity with strong authentication
- Ensure access is compliant and typical for that identity
- Follow least privilege access principles
There are a few tools available from Microsoft to help ensure you’re following these guidelines:
Azure Active Directory (AD) enables strong authentication, a point of integration for endpoint security, and the core of your user-centric policies to guarantee least-privileged access.
Multi-Factor Authentication (MFA) is an additional step built into your employee’s sign-in process. It’ll help protect your organisation against breaches due to lost or stolen credentials with strong authentication.
Conditional Access can be used to help evaluate the user trying to log in, the device they’re using, where they’re located and their behaviour.
Finally, there’s Privileged Identity Management (PIM) which can be used to ensure users are using minimal access rights by default and only have privileges for the tasks they need.
Devices
With the sharp rise of remote and hybrid working over the past 2 years, devices are now one of the biggest security risks to many organisations with employees using their personal devices. The Zero Trust strategy encourages the same security policies to be applied across all devices, whether they are corporate or personal devices through Bring Your Own Device (BYOD0).
What technologies are available to help you adopt Zero Trust? Microsoft has Endpoint Manager, which will provide you with the tools you need to manage and monitor mobile devices, desktops, virtual machines, embedded devices, and services. Allowing you to keep your data secure across all of these devices, whether they’re in the cloud or on-premises. Endpoint Manager combines popular Microsoft services such as Intune, Configuration Manager, Desktop Analytics and more.
Application
As more businesses adopt a Hybrid Working approach, critical business applications are moving into the cloud so employees can access them whether they’re at home or in the office. To get the full benefit of cloud applications and services, you must be able to provide access whilst maintaining control to protect critical data accessed via applications and APIs. Now that your employees can access your resources and apps from outside your corporate network, it’s no longer enough to have rules and policies on your firewalls. You should instead start focusing on identifying app usage patterns, assessing risk levels and business readiness of apps, preventing data leaks to non-compliant apps, and limiting access to regulated data.
Microsoft has suggested enabling Cloud Discovery and integrating Defender for Endpoint so that you can start collecting data from Windows 10 devices on and off your network. You can then create policies that will allow you to detect, and be alerted of, any risky behaviour or suspicious activity in your cloud environment.
But that’s not all you can be doing to protect your applications. Most cloud applications provide an API for consuming tenant information and receiving corresponding governance actions. Microsoft recommends you use these integrations to monitor and alert when threats and anomalies occur in your environment. You can adopt Microsoft Cloud App Security, which works with services to optimize visibility, governance actions, and usage.
Data
Data is one of your most valuable assets, and you must protect it at all costs. This is why it’s time you moved from perimeter-based data protection to data-driven protection. To help you implement effective information protection, we recommend you follow the below process, leveraging certain Microsoft technologies:
- Knowing your data – Understand your data landscape and identify important information across your cloud and on-premises environment.
- Protecting your data – Protect your sensitive data throughout its lifecycle by applying Microsoft sensitivity labels linked to protection actions like encryption, access restrictions, visual markings, and more. You can use the following tools to help protect your data; Sensitivity labels, Azure Information Protection, Cloud App Security, Double Key Encryption, Office 365 Message Encryption (OME) and SharePoint Information Rights Management (IRM).
- Prevent Data loss – Apply a consistent set of data loss prevention policies across the cloud, on-premises environments, and endpoints to monitor, prevent, and remediate risky activities with sensitive data. Leverage the following Microsoft technologies to help prevent data loss within your organisation; Data Loss Prevention Policy, Endpoint Data Loss Prevention and Microsoft Compliance Extension.
- Govern your data – Manage information lifecycle and records intelligently with in-place management, automated policies, defensible disposal, and pre-built data connectors.
Infrastructure
Your Infrastructure, whether on-premises servers or cloud-based VMs, can open you up to threats. This is why it’s important you assess for version, configuration and Just-In-Time access to strengthen your defence. Start by detecting any attacks on your infrastructure and automatically block any risky behaviour to prevent any issues.
Microsoft suggested setting the Tenant Baseline, which is a way for you to set a baseline for how your Infrastructure is meant to be running. Leveraging Azure provides you with the ability to manage all your VMs in one place using Azure Arc. Using Azure Arc, you can extend your Security Baselines from Azure Policy, your Azure Security Center (ASC) policies, and Secure Score evaluations, as well as logging and monitoring all your resources in one place
Network
We all know the castle and moat approach isn’t enough anymore. Adopting a Zero Trust strategy means that you assume that nothing behind your corporate firewall is safe.
This has drastically changed. Now there isn’t necessarily a contained/defined network to secure as people are working from home off various devices. Instead, there is a vast portfolio of devices and networks, all linked by the cloud. It’s important that you verify each request as if it originates from an uncontrolled network. There are a few Microsoft tools available to support you in protecting your network, such as; Azure Web Applications Firewall (WAF), Azure Firewall, Azure Front Door, Azure VPN Gateway and Azure Bastian.
Those were just a few of the technologies available to support you in adopting Zero Trust. But as one of Microsoft’s closest partners, we understand that enabling these aren’t always as easy as they seem. Which is why we’re here to help.
Talk to the experts
Are you wanting to find out more about the Microsoft security technologies available and how you can adopt them to implement a Zero Trust strategy? We’re one of Microsoft’s closest partners and an Azure Expert MSP. Meaning we have the knowledge and expertise to help you transform your security. We have a Zero Trust Health Check available to help you understand what your next steps should be. Simply get in touch to talk with one of our experts.
Inspire is Microsoft’s annual event for Microsoft partners. It’s a conference where Microsoft announces key product and service updates that allow partners to provide a best-in-class experience for their customers. This year’s conference was anchored in the Microsoft Cloud and the opportunities it provides customers to build powerful solutions to grow their business.
This year Microsoft made some truly exciting announcements that we’ve broken down into 4 key categories:
- Digital transformation across industries
- The future of work
- Security for the new normal
- Helping ISVs drive business growth
1. Digital Transformation across industries
Microsoft Cloud for Sustainability: a SaaS offering that enables organisations to more easily and effectively record, report, and reduce their emissions towards net zero, with plans to support water and waste tracking. The packaged offering includes SaaS offerings that connect to real-time data sources, accelerate data integration and reporting, provide accurate carbon accounting, show performance against goals, and provide intelligent insights to enable any organisation to take more effective action on sustainability.
Comment: We’re really excited by Microsoft’s efforts to increase sustainability and understand that it’s a priority for many of our customers. We’re currently looking at how we’re able to introduce Microsoft Cloud for Sustainability to our managed services alongside areas such as cost, security and performance monitoring.
2. The future of work
Since the start of the pandemic, Microsoft Teams has become the new front end for a new world of work. Microsoft has announced some exciting new products and features that are creating new categories and new possibilities for customers:
Windows 365: Windows 365 is a new way to deliver Windows 10 or Windows 11, streaming your personalised apps, settings, and content from the Microsoft cloud to any device. This allows users to maintain the familiarity of their corporate desktop with settings, applications and data consistently whether logging on from a laptop, a tablet, a Mac or a Linux device. Microsoft have given this new device independent way of working a new name; Windows 365 Cloud PC and it’s scheduled to release on 2nd August 2021.
Because Windows 365 Cloud PC is run from the Microsoft Cloud, you’ll get the all the advantages of reliability, scalability and security we’ve come to expect from Microsoft. Windows 365 makes purchasing Cloud PCs easy with predictable per-user per-month pricing, and is natively integrated across Azure AD, Microsoft Defender, Microsoft 365 applications, and Microsoft Endpoint Manager for Enterprise customers, while Business customers can leverage a simplified self-service experience on the web. Organisations will have two edition options, with multiple Cloud PC configurations based on performance needs: Windows 365 Business and Windows 365 Enterprise.
Comment: The release of Windows 365 Cloud PC is something we’re incredibly excited about as we believe that it will revolutionise the way organisations go about Hybrid Working due to its simplistic and versatile nature. We’re extremely excited to leverage Windows 365 in helping our customers work more efficiently in the new normal.
Employee Experience: A first-class example of the brand-new collaborative apps you can build in Teams is Microsoft Viva. Viva puts people at the centre, connecting them to company information, workplace insights, knowledge, and learning. Customers value Viva as an open platform that can be easily integrated with existing tools and systems and customised for business needs. Earlier this year, Microsoft announced a number of Viva partner integrations, and this week, Microsoft announced the second wave of 21 Viva partnerships and new research from The Bersin Academy.
Comment: As expected, Microsoft unveiled numerous updates around Microsoft Viva – their new employee experience platform that helps you create a work environment that puts people first. Microsoft Viva brings together communications, knowledge, learning, resources, and insights to help forge better, more inclusive employee experiences. We’re working closely with early adopters of Microsoft Viva to offer this revolutionary solution to our customers. If you’re interested in deploying Microsoft Viva with the support of Cloud Direct and Microsoft, get in touch here.
3. Security for the new normal
The world is changing, and Microsoft Security is rising to the challenges of a new normal. This year Microsoft surpassed $10 billion in security business revenue, representing more than 40 percent year-over-year growth, and were recognized as a leader in 5 Gartner Magic Quadrants and 7 Forrester Waves.
Free extended security updates for 2008/R2 and 2012 servers – only on Azure. Microsoft announced Extended Security Updates for Windows Server 2012 and 2012 R2, and SQL Server 2012, free only on Azure. Customers running 2012 releases of Windows Server and SQL Server on-premises will have the option to purchase Extended Security Updates. In addition, for customers who need more time to upgrade and modernise Windows Server and SQL Server 2008/R2, Microsoft now provide one additional year of free extended security updates only on Azure.
Comment: If you have any of the above listed servers, get in touch with one of our consultants to learn more about your options and how you’re able to take advantage of the free security updates announced by Microsoft.
Microsoft 365 Lighthouse (now in public preview): Microsoft 365 Lighthouse provides managed service providers with one central location and standard security configuration templates to secure devices, data, and users for small and medium business customers that are using Microsoft 365 Business Premium. Specifically, Microsoft 365 Lighthouse empowers partners to quickly identify and act on threats, anomalous sign-in, and device compliance alerts. Reducing management complexity as our partners scale and driving standardization across customers will allow partners to proactively manage risks and improve customers’ security posture.
Comment: As is demonstrated by our Azure Expert MSP status, we’re constantly on the hunt for solutions that allow us to provide better support for our managed service customers. We’re incredibly excited about the Microsoft 365 Lighthouse announcement and look forward to including it in our managed services to help our customers improve their security posture.
4. Helping ISVs drive business growth
Microsoft announced incredible improvements to their value proposition for ISVs, and as one of only three UK partners that are Azure Specialists for ISVs we’ve decided to do a dedicated blog post on those changes which will be available soon.
Want more information?
To get more information about these updates visit Microsoft’s Inspire 2021 Book of News. Alternatively, if you have any questions about how you’re able to leverage the above technologies or any other Microsoft technologies, get in touch with one of our experts here.
The rise of hybrid working has completely changed the security perimeter for good. Security perimeters used to be defined by your organisation’s location, as that’s where your desktops, servers and employees were. But in the hybrid workplace, this extends beyond your offices to any access point that hosts, stores, or accesses corporate resources and services. In the new world of working, employees need secure access to their resources, regardless of where they are working.
Now’s the time to rethink your security strategy. Cyber-attacks have become increasingly sophisticated, and the old castle-and-moat approach is no longer an effective method of securing your environment.
Time to ditch the castle-and-moat approach
We all know the castle-and-moat approach – defend your perimeter while assuming everything that’s already inside doesn’t pose a threat and is already cleared for access. Well, if you’re still using that mentality, it’s time to leave the castle-and-moat approach in the past. Why? It’s been proven time and time again that it doesn’t work in the modern workplace. There’s been endless data breaches as hackers have gained access inside of the firewalls and were able to seamlessly move through internal systems with minimal resistance.

Traditional security practices, such as the castle-and-moat approach, are unable to keep up with the complexity of the ever-evolving workplace. Gone the days where the ‘castle’ works in isolation as it used to. Businesses no longer have data centres for a contained network, but instead, have applications both on-premise and in the cloud with different users accessing them from multiple devices and locations.
It’s important you have a security strategy in place that’s aligned with the modern, hybrid work environment which will look at keeping anything inside and outside your perimeter safe. This is why we want to introduce you to Zero Trust, an end-to-end security strategy that’s been adopted by millions of organisations across the world to protect their technology ecosystem.
What is Zero Trust
Zero Trust Network is a security best practice model which was created back in 2010. Over a decade later, IT managers across the world are implementing Zero Trust as their security strategy. It’s never been easier to adopt a Zero Trust approach as more common technologies, such as Microsoft’s security solutions, are supporting it. Simply put, the Zero Trust concept is built on the belief that businesses shouldn’t trust anything inside or outside its perimeters and must verify anything and everything to connect its systems before granting access.
What does this mean for you? It would require a change in mindset – instead of assuming everything behind your firewall is safe, assume breach and the need to verify each request as it comes from an open network. Zero Trust encourages you “never trust, always verify”, meaning no cyber attack slips through the gaps. Having a Zero Trust security strategy means:
- Any access request should be authenticated and authorised before granting access.
- You should utilise analytics to detect and respond to any anomalies in real time. Mitigating any risks before they become a real threat.
- Microsegmentation and least privileged access principles are applied to minimize lateral movement
- Leverage analytics to identify what’s happened, if anything was compromised and how to stop it.
The three guiding principles of Zero Trust
There are three principles that a Zero Trust strategy is built on; verify explicitly, use least privileged access, and assume breach. When you have a Zero Trust strategy in place, these three principles should be at the heart of your IT and at the forefront of your mind.
|
Verify explicitly Always authenticate and authorise data points. This includes identity, location, device and workload. |
Use least privileged access
Limit user access in order to protect your data. |
Assume breach Verify that all end points are encrypted end to end. Leverage analytics to get visibility, drive threat detection and improve defences. |
These principles will help you build solid foundation to start defending the six elements Zero Trust helps you defend.
Six elements to Zero Trust
The Zero Trust security methodology is made up of six core elements: identities, devices, apps, data, infrastructure and networks. Think of these six elements as the pillars to building a Zero Trust environment. They need to be defended in order for you to stay secure, and you can do this by assuming breach.
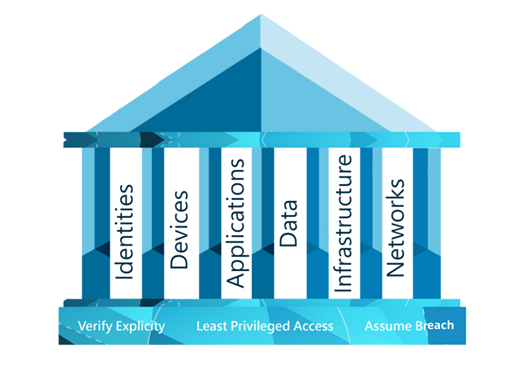
Why you should consider adopting Zero Trust
Adopting a Zero Trust strategy will benefit your business in other ways than just protecting your business. For starters, you’ll have a true sense of how secure you truly are and will be able to better manage your overall security posture.
You’ll also have the opportunity to scale back on any overlapping security spend. Businesses can often buy security products for tactical reasons that will often work in isolation to look after a single aspect of your security. Overtime there often becomes a pileup of products that aren’t delivering optimal coverage or value for money. Adopting a Zero Trust method will help you unify your security and ultimately help you save on costs as you streamline your technologies.
Finally, there is currently a huge skills gap when it comes to cyber security, and that gap is only going to grow. As more businesses identify they can no longer trust everything within their network, and realise they need to adopt a Zero Trust approach, this can often highlight a industry wide issue that businesses across the UK are currently facing a massive skills gap when it comes to Cyber Security. But Zero Trust can help this as the methodology will help give you a clear foundation to follow. Plus. if you don’t have the in house capabilities available, then you will have the option to draw upon the expertise from a company who specialises in security. Psst… we’re a Microsoft Gold Security Partner and have a Zero Trust Assessment available, which brings us nicely onto wrapping up this blog post.
Looking to implement Zero Trust
The truth is, building Zero Trust within an organisation doesn’t happen overnight. There’s a lot of planning that’s involved. Microsoft suggests you start by evaluating your current environment, available resources and priorities. From there you can start pulling together a plan to implement a Zero Trust strategy that meets your business needs.
Implementing Zero Trust in your organisation can often seem overwhelming. The best first step is to ensure you have the right technology in place to help you enable Zero Trust. Microsoft Technologies have the security tools and features you need to implement Zero Trust – Enabling you to gain control over your organisation’s security. Head over to Microsoft’s website to find out how Bridgewater leveraged Microsoft 365 to deploy a Zero Trust security model.
As an Azure Expert MSP and Microsoft Security Gold Partner, we’re in a unique position to help you adopt Zero Trust within your organisation. Not only could we help you deploy Microsoft technologies, but we’ll also help you implement the Zero Trust best practices and framework. Simply get in touch to find out more.
According to a recent government study, two in five businesses in the UK have reported having experienced cybersecurity breaches or attacks in the last 12 months. Of these, one in five respectively ended up losing money, data or other assets. With cybercrime at an all-time high, it’s become increasingly important for organisations to understand how their security measures up.
Thankfully, by having Microsoft in your corner, you’re already half of the way there. As part of their $1bn annual investment in security, Microsoft has created the Microsoft Secure Score – a security tool that helps you measure and understand your organisation’s security posture.
So, what exactly is your Microsoft 365 Secure Score?
Check out this short clip from one of our Secure Score webinars, where we give a quick overview of what the Microsoft Secure Score is:
As a Microsoft 365 user, you’ll have access to a Secure Score that’s located within your Security Centre. Your Secure Score dashboard gives you access to robust visualisations of metrics, trends, integration with Microsoft products, score comparison with similar organisations, and much more. Your overall score is displayed as a percentage, with a higher number indicating a stronger security posture. Pretty straight forward, huh?
In a nutshell, your Secure Score helps you:
- Report on the current state of your organisation’s security posture.
- Improve your security posture by providing you with discoverability, visibility, guidance, and control.
- Compare your organisation’s security with industry benchmarks and establish security key performance indicators (KPIs).
How to start improving your Microsoft Secure Score
Alongside your score, you’ll have a list of recommended actions that can help improve your security rating. The recommendations will highlight the maximum score you’re able to achieve for each control and how those improvements could potentially increase your overall Secure Score. Thus, allowing you to identify which improvements will have the biggest impact on your overall security. It’ll also show you the number of resources affected by each control and each resource’s impact on your overall score.
You’re given points for the following actions:
- Configuring recommended security features
- Doing security-related tasks
- Addressing the improvement actions with a third-party application or software, or an alternate mitigation
So, how exactly is your score calculated? Your Secure Score considers your entire Microsoft security set-up and analyses which controls you’ve enabled and set up. The percentage itself is calculated using the formula below. You can find out more about how this is calculated on Microsoft’s website.

Whilst Microsoft provides a list of recommended improvements along with the impact they will have on your overall score, these improvements are simply based on best practices and won’t always be the best option for your business. It is therefore important that you really take some time to interpret the recommendations in the context of your business or speak to an expert about it (Psst… That’s us!).
Need help navigating your Secure Score?
When looking to improve your score, it’s best to work with an Azure Expert MSP and Gold Security partner to help you identify which Microsoft recommendations are best aligned with your organisations policies. We’ve helped numerous businesses improve their security, and we can help you too.
We’re currently running one-on-one Secure Score workshops where our experts will analyse your security and help you create an enhancement plan. Want to find out more? Follow the link below to get in touch with one of our experts and to see if you qualify.
Over the past year cyber security has become an increasingly hot topic, and for good reason. A recent study by the UK government found that two in five businesses (39%) and one in four charities (26%) have reported having experienced cyber security breaches or attacks in the last 12 months. In this article, we’ll take a dive into Microsoft’s approach to integrated security and discuss the differences between some of the most common Microsoft 365 licence types.
Microsoft’s Integrated Approach to Security
With hundreds of security solutions out there, it can be hard to know where to start with securing your organisation. Microsoft’s Integrated Security takes a holistic approach to securing your organisation’s IT and data environment across 4 key vectors:

Identity & Access Management
Identity and access management (IAM) is the first line of defence and foundation of any secure digital working environment. It is a framework of policies, processes and technology that enables the management of user identities. It uses user credentials and other authentication methods like Multi-factor authentication (MFA) to determine whether the user using them is who they are claiming to be. Once their identity has been authenticated, the user is authorized to access the resources that they have been granted permission to.
Threat Protection
Threat Protection refers to a category of security solutions that defend against malware or hacking-based attacks that target sensitive data. It monitors activity across your entire digital estate and ensures that threats are rapidly identified and quarantined. Some of Microsoft’s most notable Threat Detection solutions include:
- Microsoft 365 Defender, which is a unified pre- and post-breach enterprise defence suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
- Defender for Endpoint, which is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats.
- Microsoft Cloud App Security, which is a cloud access security broker (CASB) that provides multifunction visibility, control over data travel, and sophisticated analytics.
Information Protection
Information Protection solutions help keep sensitive data secure irrespective of where it’s stored or where it travels. Microsoft’s Information Protection technologies allow you to set up and quickly configure data security policies with sensitivity labels. By creating sensitivity labels with pre-configured rules, you’re able to conveniently assign security policies to files that are applied regardless of where that file is stored.
Security Management
The Microsoft 365 security centre combines protection, detection, investigation, and response to email, collaboration, identity, and device threats, in a central portal. It has been designed to allow for quick access to critical security information, so you’re able to stay on top of your organisation’s security in real-time. The security centre includes:
- Microsoft Defender for Office 365, which helps organisations secure their enterprise with a set of prevention, detection, investigation and hunting features to protect email, and Office 365 resources.
- Microsoft Defender for Endpoint, which delivers preventative protection, post-breach detection, automated investigation, and response for devices in your organization.
- Microsoft 365 Defender, which is part of Microsoft’s Extended Detection and Response (XDR) solution that leverages the Microsoft 365 security portfolio to automatically analyse threat data across domains and build a picture of an attack on a single dashboard.
Comparing Common Microsoft 365 Licence Types
Each of the above mentioned vectors are protected by a variety of powerful security features that are deployed based on your Microsoft 365 or Office 365 licence type. These security features include:

With the above in mind, let’s take a look at how some of the common Microsoft 365 and Office 365 licence types are able to safeguard your organisation’s apps and data.
Microsoft 365 Business Standard vs. Microsoft 365 Business Premium
Microsoft 365 Business Standard is a licence for businesses who need Microsoft Office applications across multiple devices as well as business email, cloud file storage and online meetings and chat. Microsoft 365 Business Premium includes everything Microsoft 365 Business Standard has to offer, with the addition of powerful security features to safeguard your business.
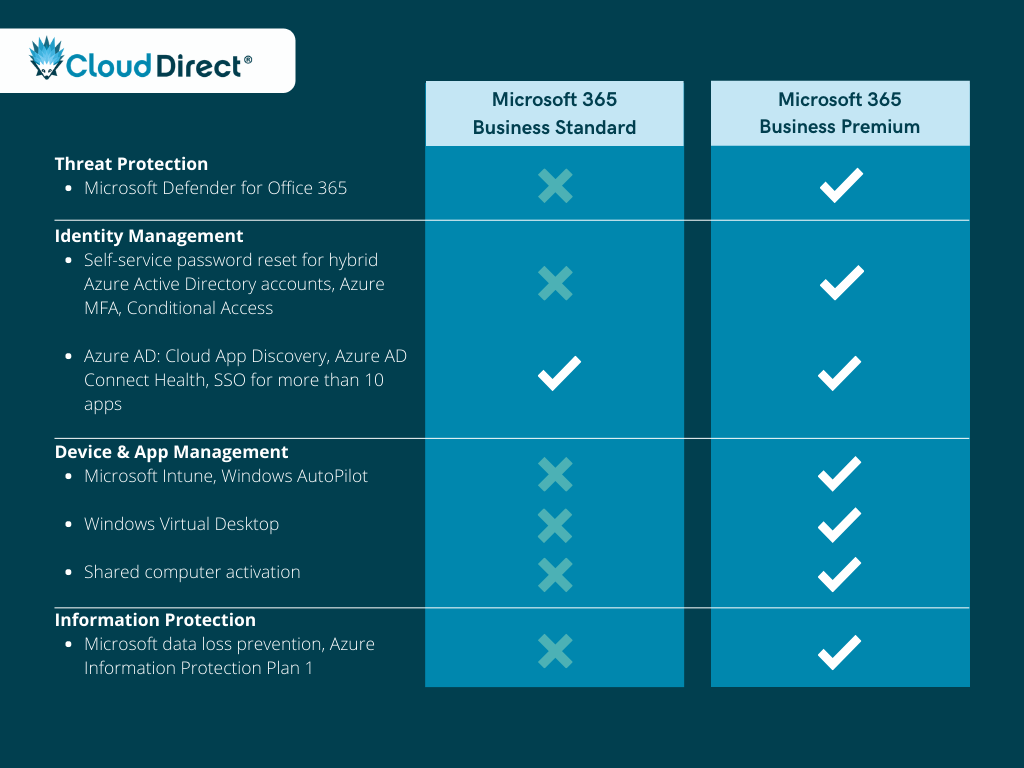
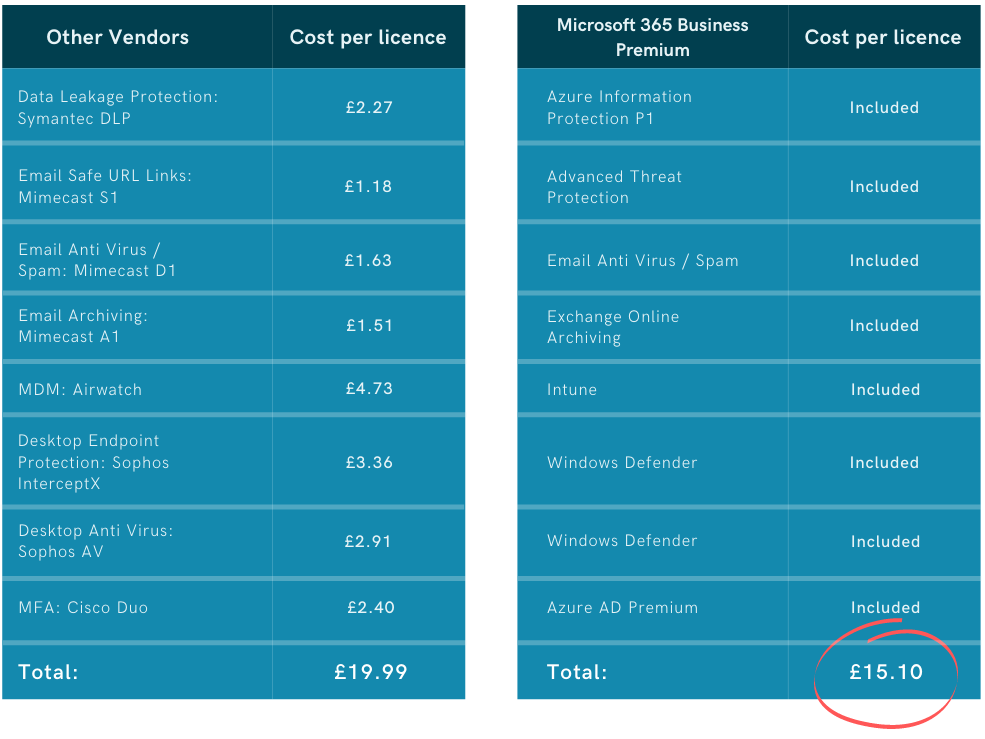
Why upgrade to Premium?
As is made clear by the above comparison, Microsoft 365 Business Premium is able to do a much better job of securing your organisation’s apps and data. While these additional security features do come with a bit of an extra cost, it’s a small price to pay for significantly reducing the risk of falling victim to cyber attacks. A 2018 study done by Kaspersky, found that the average cost of a SMB data breach is around £85,000. Additionally, when comparing the Microsoft 365 Business Premium licence fee to what it would cost to deploy these security features using third-party vendors, it’s clear that Business Premium offers excellent value for money:
Office 365 E3 vs. Microsoft 365 E3
The Microsoft 365 Enterprise plans effectively mirror the Office 365 Enterprise plans, with the addition of a Windows 10 Enterprise licence and Enterprise Mobility and Security (EMS) features. While Microsoft 365 Business Premium might be suitable for most businesses under 300 seats, it does have it’s limitations. This is where Microsoft 365 E3 comes into play. Microsoft 365 E3 can be seen as the minimum requirement for organisations that have complex or regulatory requirements around security and compliance.
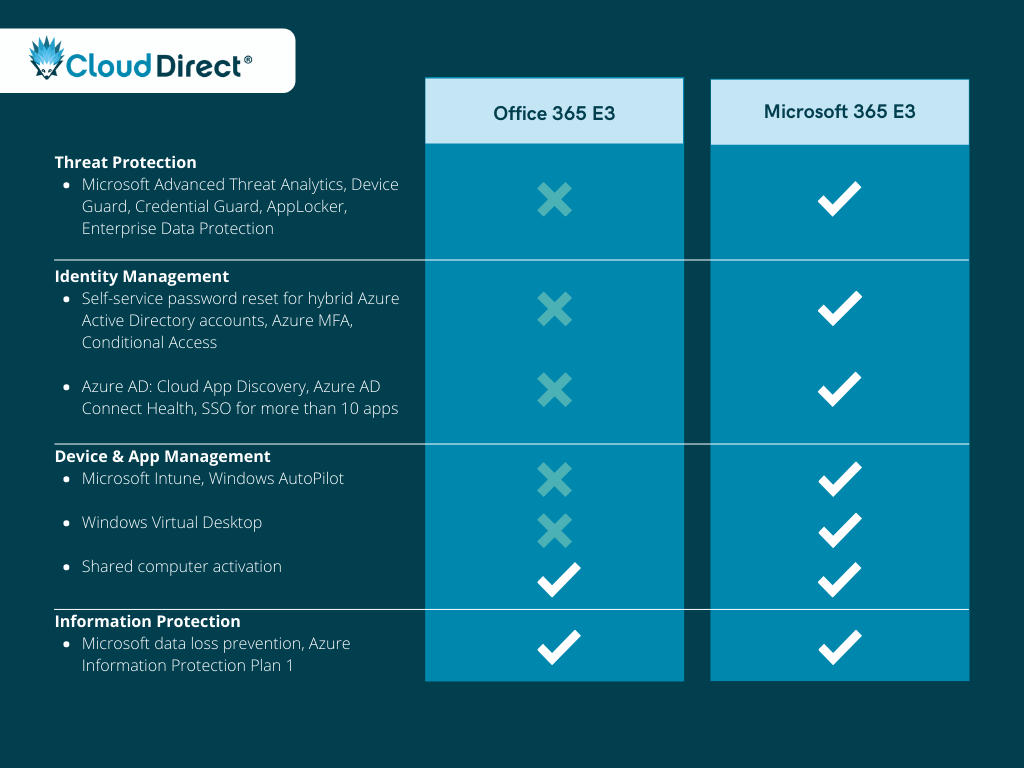
Why upgrade to Microsoft 365 E3?
As was the case with the previous comparison, Office 365 E3 will only provide you with the necessary tools to support your organisation’s productivity and collaboration, and won’t give you adequate protection against cyber attacks. Microsoft 365 E3 is built for businesses who want the best in productivity and collaboration while operating in a secure and compliant environment.
Microsoft 365 E3 vs. Microsoft 365 E5
Microsoft 365 E5 is Microsoft’s flagship licence and is the most complete productivity and security solution available. This licence is a significant step-up from Microsoft 365 E3, and includes many additional features, such as: Teams Voice capabilities, Power BI Pro licences and a variety of top-tier security technologies.

Why upgrade to Microsoft 365 E5?
As Microsoft’s ‘Hero’ licence type, Microsoft 365 E5 is built for organisations that want to have the best in productivity, security, and compliance. The additional security features allow you to have greater control and visibility over your Microsoft 365 environment. You’ll benefit from all of Microsoft’s best security features, including Microsoft 365 Defender for Endpoint, Office 365 and Identity, Azure Active Directory Premium Plan 2, and Cloud App Security. Additionally, The E5 licence gives you the ability to configure and automate security policies and regulations, which, in turn, leads to significantly less administrative overheads.
Conclusion
While there isn’t any one licence that is suitable for all organisations, we hope that you’ve gained a deeper understanding of Microsoft’s approach to security and how the various licences are able to safeguard your business. It’s important to understand that simply purchasing a high-end licence, such as Microsoft 365 E5, will not secure your working environment. These licences need to be properly configured and continuously monitored to protect your business.
Need help making sense of your organisation’s security? As an Azure Expert MSP and Gold Security Partner, our team of in-house security experts are well-equipped to help you understand which Microsoft 365 licence is best for you and how you’re able to leverage the power of Microsoft’s security solutions. So what are you waiting for? Get in touch via the link below:
According to a recent study by the Government’s Department for Digital, Culture, Media and Sport, two in five businesses reported having cybersecurity breaches or attacks in the last 12 months. Of these, one in five respectively ended up losing money, data or other assets. With security breaches happening more frequently, it’s increasingly important that your business stays resilient.
When it comes to improving your business’s security, Microsoft has got your back. They invest over $1billion in security annually. Want to learn what this means for you? Discover four ways Azure can improve your security in our recent blog post.
One of the tools Microsoft has created is the Azure Secure Score, which has been designed to sit at the heart of your security. Microsoft created the Azure Secure Score to help give you guidance on their security best practices.
Firstly, what is the Microsoft Azure Secure Score?
All Microsoft Azure customers have access to a Secure Score that can be located within the Security Center. Your Secure Score will help you to not only gain an understanding of your current Azure security but also identify ways in which you can improve your overall security posture. Your score will be displayed as a percentage, making it easy to understand and measure.
But how is your score calculated? The Secure Score considers your entire Azure security set-up and analyses what controls you’ve enabled and set up. The percentage itself is calculated using the formula below. You can find out more about how this is calculated on Microsoft’s website.

Alongside your score, you’ll have a list of recommended actions that can help improve your security rating. The recommendations will highlight the maximum score you’re able to achieve for each control and how those improvements could potentially increase your overall Secure Score. Thus, allowing you to identify which improvements will have the biggest impact on your overall security. It’ll also show you the number of resources affected by each control and each resource’s impact on your overall score.
How to start improving your Azure Secure Score
Whilst Microsoft provides a list of recommended improvements along with the impact they will have on your overall score, these improvements are simply based on best practices and won’t always be the best option for your business. It is therefore important that you really take some time to interpret the recommendations in the context of your business or speak to an expert about it (Psst… That’s us!).
When looking to improve your score, it’s best to work with an Azure Expert MSP to help you identify which Microsoft recommendations are best aligned with your organisations policies. As an Azure Expert MSP, we’ve helped numerous businesses improve their security, and we can help you too.
We’re currently running Secure Score workshops where our experts will analyse your security and help you create an enhancement plan. Want to find out more? Talk to our experts and sign up today.
When migrating to the cloud it can be easy to jump in headfirst. But you must take a step back and review things before you start your cloud journey. Migrating to the cloud provides you with the chance to think ahead and create an environment that allows you to scale and innovate with ease.
Whilst some workloads can be easily migrated to Azure with little adaption – these are the ones we target in our first phase migration – many will need to be re-configured for performance and cost optimisation.
To realise the true potential of Azure and build a scalable base, you should start with Azure Landing Zone. They are the fundamental structures that put security and optimal performance at the core of your cloud environment.
What is an Azure Landing Zone?
A Landing Zone is a key concept of Microsoft’s Cloud Adoption Framework that allows you to build a secure foundation to scale and innovate with ease. Not familiar with the Cloud Adoption Framework? Fear not as we have a beginner’s guide that covers everything you need to know. Microsoft has created the Landing Zone based on best practices and cloud services for you to leverage as part of your migration, mitigating any complexities you may face.
A Landing Zone can be deployed at any stage – whether you’re in the process of deploying your first production application in Azure or operating a complex portfolio of tech platforms and workloads. Landing Zones have been created to be both scalable and modular – you’ll have repeatable environments with the same configuration and controls allowing you to scale but also have a modular environment thanks to its common set of design areas that can be extended to support specific technologies.
Why you should deploy a Landing Zone
It should be clear by now that to ensure a safe take-off in Azure you need a Landing Zone in place, enabling you to have a faster, more secure and efficient migration. Which is ultimately what you’re trying to achieve, right? Having a Landing Zone in place before you start migrating your infrastructure provides you with a solid foundation for you to future-proof your IT. Plus you’ll have access to Microsoft cloud services and best practices that set you up for success. But that’s not all. You’ll also be able to benefit from:
Increased speed |
Increased scalability |
Best security and performance |
Five principles for deploying a landing zone
Microsoft has put together five key principles that you should be leveraging when deploying a Landing Zone.
- Utilise Networking Services – Add or remove workloads without disrupting the rest of your environment and leverage connectivity to bring your applications together.
- Identity Management – Within a Landing Zone, you’ll be able to set identity rules so only certain employees will be able to access data – providing you with better user management. You’ll be able to leverage Single Sign-On, Role-Based Access Control and Authentication to enable effective identity management.
Once you have the first two principles in place, you’ll be able to start migrating low-risk workloads. When you’ve migrated any low-risk workloads, you’ll then be in a place to start looking at the next three principles.
- Governing your environment – Microsoft will enable you to govern your environment with compliance policies to ensure you’re meeting industry regulations.
- Leverage Microsoft security – You’ll be able to leverage Microsoft security controls to protect both data at rest and in transit, allowing you to detect threats before it’s too late.
- Manage your environment – Once you have your Landing Zone in place you’ll not only have a secure space for your environment but also the tools in place to effectively monitor performance.
When you’ve got all of these three principles in place, you’ll be able to accelerate your migration and now have a secure foundation to move any business-critical workloads into Azure.
Ready to deploy a Landing Zone?
As an accredited Microsoft Azure Expert MSP and Cloud Adoption Framework ready partner, we’re able to help you deploy a landing zone. Simply get in touch with our experts.
If the past year has taught us anything, it’s that how we work is far more important than where we work from. Across the globe, remote working has become the norm and it’s opened up a plethora of opportunities for the modern workplace. Which, by the way, will undoubtedly be hybrid.
Hybrid Working is on the rise and with an end to the COVID-19 pandemic in sight, we’ve already seen an uplift in businesses adapting to this way of working. One such example is that of Nationwide, the UK’s largest building society who recently told 13,000 of their staff to ‘work anywhere’. And they’re in good company. The Work Trend Index: 2021 Annual Report, found that:

So, what exactly is the Hybrid Workplace and Hybrid Working?
Apart from being a slick sounding buzzword, the Hybrid Workplace is a business model that’s geared towards the need for increased flexibility in modern business. It’s by no means a new concept; however, it has become increasingly relevant as more and more businesses plan their post-pandemic way of working.
Hybrid Working allows some employees to work remotely, be that in a coffee shop or at home, while others work on-premises. Having your cleaning staff work from home probably isn’t the best idea, however, other teams such as Development and Marketing could greatly benefit from this model.
“Over the past year, no area has undergone more rapid transformation than the way we work. Employee expectations are changing, and we will need to define productivity much more broadly — inclusive of collaboration, learning, and wellbeing to drive career advancement for every worker, including frontline and knowledge workers, as well as for new graduates and those who are in the workforce today. All this needs to be done with flexibility in when, where, and how people work.” – Satya Nadella, CEO at Microsoft
The benefits of Hybrid Working
While there are several factors to consider before implementing Hybrid Working, such as technology, the nature of your work and the socioeconomic factors that may inhibit your workforce’s ability to work from home, Hybrid Working carries significant benefits when implemented correctly.
1. Improved productivity
A well-structured Hybrid Workplace creates a culture that empowers employees to work to their strengths. Through increased flexibility and independence, employees have the freedom to work when and where they are most productive. Employees will be able to experience the best of both worlds by using the office for scheduling on-premises days for meetings and collaboration, and remote days for tasks that require focus.
In an interview with BBC, Baruch Silverman, founder of personal finance website The Smart Investor, said: “We try to use home working days less for video sessions and more for the tasks that require concentration. A task that may take several hours in the office may be completed in just an hour or two at home.”
“We try to use home working days less for video sessions and more for the tasks that require concentration.” – Baruch Silverman, founder of The Smart Investor
2. Increased employee wellness and satisfaction
Mental wellness
Hybrid Working grants employees the ability to structure work around the rest of their lives, not the other way around. It removes the stress of everyday commuting and allows employees to work without the pressure of only being able to tend to non-work-related commitments when they get home after a long day at the office.
Physical wellness
Working from home provides people with disabilities or medical conditions the chance to work comfortably while staying connected. Having a more flexible working schedule allows employees to accommodate healthy eating habits and a regular exercise routine. You’re also able to decrease health exposure risks. Fewer in-house employees mean you’re able to lower the risk of colds, flu, or any other illnesses spreading around the office.
3. Remove geographical restrictions when recruiting new talent
Removing geographical restrictions allows businesses to access larger talent pools by leaning on remote work as a permanent fixture of talent acquisition. The Work Trend Index: 2021 Annual Report found that Forty-six percent of remote workers are planning to move to a new location in the next year because they can now work remotely. The report also noted that remote job postings on Linkedin increased more than 5 times between March and December 2020. By recruiting nationally (or even globally), you’re able to build teams with rich cultural and experiential diversity as well as capitalise on time-zone differences. Thus, allowing you to offer 24/7 customer support or the ability to bring in some extra brainpower during peak business hours.

Become an attractive forward-thinking employer
Less geographical restrictions mean more opportunities for jobseekers. Gone are the days where you could attract and retain talent by simply offering them a flashy salary. As we start transitioning to the new way of working, employees will come to expect flexibility and consideration towards their well-being. It’s therefore crucial that you position yourself as a forward-thinking employer by having the right technology and an effective hybrid working strategy in place.
4. Cost savings
With a flexible workforce, the need for fixed office space changes – allowing you to make significant savings on costly overheads such as electricity and rent. It’s common practice among hybrid companies to have a small office space for on-premise staff and separate meeting rooms and hot-desking areas for employees with irregular working patterns. These working areas may be situated in-house or rented from shared workspace companies like WeWork.
5. Be prepared for an uncertain future
The COVID-19 pandemic has shown us that life as we know it can be flipped upside down in an instant, which is why it’s crucial that businesses remain agile and prepared for change. The Hybrid Working model empowers you to do this by already having the right technology, structure and employees in place to adapt to unexpected circumstances.
Conclusion
While there is still a lot of uncertainty about the future of work, there is also a massive opportunity for forward-thinking businesses to get a better handle on employee well-being and productivity, while benefiting from the cost efficiencies of Hybrid Working. Now is the perfect time for organisations to establish their Hybrid Working strategy and take advantage of the significant cost savings of diverting spend from physical assets to technology. As is always the case, the businesses who fully embrace change with a growth mindset are the ones who will develop a better workplace for everyone.
Ready to prepare your business for Hybrid Working?
We recently hosted the first instalment of our new webinar series: Preparing for the Hybrid Workplace, where we took a dive into how you can set your telephony up for success with Teams Voice. To watch the recording and get caught up, visit this page. We also recommend you keep an eye on our events page to stay up to date with all our upcoming webinars and workshops.
For more information on how you can prepare for Hybrid Working, get in touch with us via the link below:





